Ans. As
computers and other digital devices have become essential to business and
commerce, they have also increasingly become a target for attacks. In order for
a company or an individual to use a computing device with confidence, they must
first be assured that the device is not compromised in any way and that all
communications will be secure.
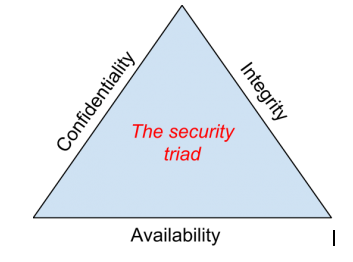
The security triad
The
Information Security Triad: Confidentiality, Integrity, Availability (CIA)
Confidentiality
When protecting information, we want to be able to restrict
access to those who are allowed to see it; everyone else should be disallowed
from learning anything about its contents. This is the essence of
confidentiality. For example, federal law requires that universities restrict
access to private student information. The university must be sure that only
those who are authorized have access to view the grade records.
Integrity
Integrity is the assurance that the information being
accessed has not been altered and truly represents what is intended. Just as a
person with integrity means what he or she says and can be trusted to
consistently represent the truth, information integrity means information truly
represents its intended meaning. Information can lose its integrity through
malicious intent, such as when someone who is not authorized makes a change to
intentionally misrepresent something. An example of this would be when a hacker
is hired to go into the university’s system and change a grade.
Integrity can also be lost
unintentionally, such as when a computer power surge corrupts a file or someone
authorized to make a change accidentally deletes a file or enters incorrect
information.
Availability
Information availability is the third part of the CIA
triad. Availability means that information can be accessed
and modified by anyone authorized to do so in an appropriate timeframe.
Depending on the type of information, appropriate timeframe can
mean different things. For example, a stock trader needs information to be
available immediately, while a sales person may be happy to get sales numbers
for the day in a report the next morning. Companies such as Amazon.com will
require their servers to be available twenty-four hours a day, seven days a
week. Other companies may not suffer if their web servers are down for a few
minutes once in a while.
Measures against threats for security….
·
Install Anti-Virus Software.
Ensure that reputable anti-virus software is installed on all computers. This should include all servers, PCs and laptops. If employees use computers at home for business use or to remotely access the network, these PCs should also have anti-virus software installed.
Ensure that reputable anti-virus software is installed on all computers. This should include all servers, PCs and laptops. If employees use computers at home for business use or to remotely access the network, these PCs should also have anti-virus software installed.
·
Ensure that the anti-virus software
is up to date.
Everyday new computer viruses are being released and it is essential that businesses are protected from these viruses by keeping the anti-virus software up to date. If possible, companies should look at policies whereby computers that do not have the most up to date anti-virus software installed are not allowed to connect to the network.
Everyday new computer viruses are being released and it is essential that businesses are protected from these viruses by keeping the anti-virus software up to date. If possible, companies should look at policies whereby computers that do not have the most up to date anti-virus software installed are not allowed to connect to the network.
·
Employ a firewall to protect networks.
As computer viruses can spread by means other than email, it is important that unwanted traffic is blocked from entering the network by using a firewall. For users that use computers for business away from the protection of the company’s network, such as
As computer viruses can spread by means other than email, it is important that unwanted traffic is blocked from entering the network by using a firewall. For users that use computers for business away from the protection of the company’s network, such as
- Filter
all email traffic.
All incoming and outgoing email should be filtered for computer viruses. This filter should ideally be at the perimeter of the network to prevent computer viruses. Emails with certain file attachments commonly used by computer viruses to spread themselves, such as .EXE, .COM and .SCR files, should also be prevented from entering the network. - Educate
all users to be careful of suspicious e-mails.
Ensure that all users know to never open an attachment or to click on a link in an email they are not expecting. Even when the email is from a known source, caution should be exercised when opening attachments or clicking on links in emails. Criminals use the trust placed in an email contact you know to trick you into clicking on a link or attachment.
An Information Security Plan (ISP) is
designed to protect information and critical resources from a wide range of
threats in order to ensure business continuity, minimize business risk, and
maximize return on investments and business opportunities. Information
Technology (IT) security is achieved by implementing a suitable set of
controls, including policies, processes, procedures, organizational structures,
and software and hardware functions. These controls need to be established,
implemented, monitored, reviewed and improved, where necessary, to ensure that
the specific security and business objectives of Michigan Technological
University are met. This plan governs the privacy, security, and
confidentiality of University data, especially highly sensitive data, and the
responsibilities of departments and individuals for such data. IT security
measures are intended to protect information assets and preserve the privacy of
Michigan Tech employees, students, sponsors, suppliers, and other associated
entities. Inappropriate use exposes Michigan Tech to risks including virus
attacks, compromise of network system services and legal issues.
The purpose of this document is to ensure that
appropriate measures are put in place to protect corporate information and the
Information Technology Services (ITS) systems, services and equipment of the
Federation University Australia and associated infrastructure.
The objectives of the Information Security Policy are:
·
To
secure the University’s assets against theft, fraud, malicious or accidental
damage, breach of privacy or confidentiality; and
·
To
protect the University from damage or liability arising from the use of its ITS
facilities for purposes contrary to the Federation University Australia
Legislation and Policies.


0 comments:
Post a Comment
Let us know your responses and feedback